| IEEE | M. Nazarewicz, D. D. Jain, M. Matos, and B. Rodriguez, “Be my guest: Welcoming interoperability into IBC-incompatible blockchains,” 2025 55th Annual IEEE/IFIP International Conference on Dependable Systems and Networks – Supplemental Volume (DSN-S), Naples, Italy, Jun. 2025, pp. 160–166, doi:10.1109/DSN-S65789.2025.00057 I’m delighted to share my paper I’ve presented at the IEEE/IFIP International Conference on Dependable Systems: ‘Be My Guest: Welcoming Interoperability into IBC-Incompatible Blockchains’. It introduces the concept of a guest blockchain which runs on top of a blockchain and provides features necessary to support the Inter-Blockchain Communication (IBC) protocol. This enables trustless cross-chain interoperability between blockchains which would otherwise not support IBC-based communication. We demonstrate our approach by deploying the guest blockchain on Solana connecting it to the Cosmos ecosystem with performance comparable to native IBC implementations.Updated on the 31st of July to reflect the fact deadline for both petitions have now passed. The dystopian interpretation of the ‘you’ll own nothing and be happy’ phrase feels increasingly prescient.1 As corporations hide behind lengthy Terms of Service and End User License Agreements,2 the concept of ownership becomes alarmingly ambiguous. This erosion of consumer rights has given rise to the Stop Killing Games (SKG) movement. In 2015 I’ve stumbled upon the Classic Tetris World Championship. Even though I’d never played NES Tetris, I started following the event with interest. I keenly remember watching the historic 2018 final which was a prelude to the next generation of players picking up the game. In contrast, world of racing games offer an example of fleeting ownership. While generations continue to enjoy NES Tetris, with a 13-year-old famously ‘beating’ the game 34 years after its release,3 Ubisoft’s 2014 game The Crew didn’t even last a decade. In 2024, Ubisoft didn’t just shut down the servers; it began revoking players’ licenses, seemingly doing everything in its power to ensure the game couldn’t be preserved or revived by the community. In the previous post, I criticised Rust’s contribution process, where a simple patch languished due to communication hurdles. Rust isn’t unique in struggling with its process. This time, the story is about Python. Parsing HTML in PythonAs its name implies, the html.parser module provides interfaces for parsing HTML documents. It offers an HTMLParser base class users can extend to implement their own handling of HTML markup. Of our interest is the unknown_decl method, which ‘is called when an unrecognised declaration is read by the parser.’ It’s called with an argument containing ‘the entire contents of the declaration inside the <![...]> markup.’ For example: from html.parser import HTMLParser
class MyParser(HTMLParser):
def unknown_decl(self, data: str) -> None:
print(data)
parser = MyParser()
parser.feed('<![if test]>')
# Prints out: if test
# (unless Python 3.13.4+, see below)
parser.feed('<![CDATA[test]]>')
# Prints out: CDATA[testIn November 2015, rmcgibbo opened Twine Issue #153. Less than two months later, he closed it with no explanation. The motive behind this baffling move might have remained an unsolved Internet mystery if not for one crucial fact: someone asked and rmcgibbo was willing to talk:  thedrow on Dec 31, 2015 Contributor Were you able to resolve the issue?
 rmcgibbo on Dec 31, 2015 Author No. I decided I don’t care.
We all had such moments, and this humorous exchange serves as a reminder that certain matters are not worth stressing about. Like Marcus Aurelius once said, ‘choose not to be harmed — and you won’t feel harmed.’ However, instead of discussing philosophy, I want to bring up some of my experiences to make a point about contributions to free software projects. The two pull requestsRather than London and Paris, this tale takes place on GitHub and linux-kernel mailing list. The two titular pull requests (PRs) are of my own making and contrast between them help discuss and critique Rust’s development process. In my previous post, I mentioned an ancient C++ technique of using ((X*)0)->f() syntax to simulate static methods. It ‘works’ by considering things from a machine code point of view, where a non-virtual method call is the same as a function call with an additional this argument. In general, a well-behaving obj->method() call is compiled into method(obj). With the assumption this is true, one might construct the following code: struct Value {
int safe_get() {
return this ? value : -1;
}
int value;
};
void print(Value *val) {
printf("value = %d", val->safe_get());
if (val == nullptr) puts("val is null");
}Will it work as expected though? Draw an arbitrary triangle with corners A, B and C. (Bear with me; I promise this is a post about undefined behaviour). Draw a line parallel to line BC that goes through point A. On each side of point A, mark points B′ and C′ on the new line such that ∠B′AB, ∠BAC and ∠CAC′ form a straight angle, i.e., ∠B′AB + ∠BAC + ∠CAC′ = 180°. Observe that line AB intersects two parallel lines: BC and B′C′. Via proposition 29, ∠B′AB = ∠ABC. Similarly, line AC intersects those lines, hence ∠C′AC = ∠ACB. We now get ∠BAC + ∠ABC + ∠ACB = ∠BAC + ∠B′AB + ∠C′AC = 180°. This proves that the sum of interior angles in a triangle is 180°.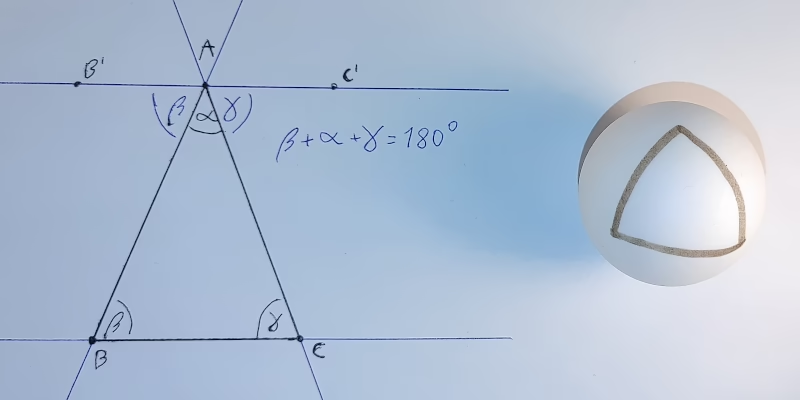 Now, take a ball whose circumference is c. Start drawing a straight line of length c/4 on it. Turn 90° and draw another straight line of length c/4. Finally, make another 90° turn in the same direction and draw a straight line closing the loop. You’ve just drawn a triangle whose internal angles sum to over 180°. Something we’ve just proved is impossible‽ There is no secret. Everyone sees what is happening. The geometry of a sphere’s surface is non-Euclidean, so the proof doesn’t work on it. The real question is: what does this have to do with undefined behaviour?  Pracownik helpdesku ubrany we frak. Pracownik helpdesku ubrany we frak.| BibTeX | @article{Stangret2005,
title = {Informatycy najgorzej ubrani},
author = {Michał Stangret},
journal = {Gazeta Praca},
year = 2005,
month = nov,
day = 25,
url = {https://web.archive.org/web/20051218031319/http://praca.gazeta.pl/gazetapraca/1,67728,3032865.html}
} |
|---|
| APA | Stangret, M. (2005). Informatycy najgorzej ubrani. Gazeta Praca (25 XI 2005). web.archive.org/web/20051218031319/http://praca.gazeta.pl/gazetapraca/1,67728,3032865.html Przeglądając archiwa swoich starych dysków, natknąłem się na niesłychanie ciekawy artykuł z Gazety Praca. Czas zrobił swoje i na stronie Gazety już go niestety nie ma,1 a szkoda aby zniknął po nim ślad. Pozwolę więc sobie go zacytować w całości, aby przetrwał dla potomności: Informatycy najgorzej ubraniMichał Stangret, 2005-11-25 Są przepoceni, rzadko myją włosy i noszą flanelowe koszule wciągnięte w spodnie. Komputerowcy zajęli pierwsze miejsce w rankingu najgorzej ubranych zawodów. Dostało się też księgowym, urzędnikom i dziennikarzom.
‘Ctrl+D in terminal is like pressing Enter,’ Gynvael claims. A surprising proclamation, but pondering on it one realises that it cannot be discarded out of hand. Indeed, there is a degree of truth to it. However, the statement can create more confusion if it’s made without further explanations which I provide in this article. To keep things focused, this post assumes terminal in canonical mode. This is what one gets when running bash --noediting or one of many non-interactive tools which can read data from standard input such as cat, sed, sort etc. Bash, other shells and TUI programs normally run in raw mode and provide their own line editing capabilities. Mark Rober’s video where he fooled Tesla car into hitting fake road has been making rounds on the Internet recently. It questions Musk’s decision to abandon lidars and adds to the troubles Tesla has been facing. But it also hints at a more general issue with automation of complex systems and artificial intelligence. A drawing of a Tesla car with self-driving technology engaged. A drawing of a Tesla car with self-driving technology engaged. ‘Klyne and I belong to two different generations,’ testifies Pirx in Lem’s 1971 short story Ananke. ‘When I was getting my wings, servo-mechanisms were more error-prone. Distrust becomes second nature. My guess is… he trusted in them to the end.’ The end being the Ariel spacecraft crashing killing everyone onboard. If Klyne put less trust in ship’s computer, could the catastrophe be averted? We shall never know, mostly because the crash is a fictional story, but with proliferation of so called artificial intelligence, failures directly attributed to it has happened in real world as well: In 2004, Brady Haran published the infamous Astounding: \(1 + 2 + 3 + 4 + 5 + \cdots = -\frac{1}{12}\) video in which Dr Tony Padilla demonstrates how sum of all natural numbers equals minus a twelfth. The video prompted a flurry of objections from viewers rejecting the result. But riddle me this: Would you agree the following equation is true: \[1 + \frac{1}{2} + \frac{1}{4} + \cdots = 2\] Obviously the equation does not hold. How could it? The thing on the left side of the equal sign is an infinite series. The thing on the right side is a real number. Those are completely different objects therefore they cannot be equal. Anyone saying the two are equal might just as well say \(\mathbb{N} = 🐘\) (and while I grant you that elephants are quite large, they’re not sets of natural numbers). And yet, people usually agree the infinite sum equals 2. Why is that? They use ‘mathematical trickery’ and redefine the meaning of the equal sign. Indeed, \(1 + \frac{1}{2} + \frac{1}{4} + \cdots\) does not equal 2. Rather, given an infinite series \((a_n)\) where \(a_n = 2^{-n}\), we can define an infinite series \((S_n)\) where \(S_n = \sum_{0}^{n} a_n\) and only now we get: \[\lim_{n\to\infty} S_n = \lim_{n\to\infty} 2 - \frac{1}{2^n} = 2\] But that’s a different equation than the one I’ve enquired about. Even though Bitcoin is technically Turing complete, in practice implementing a non-trivial computation on Bitcoin is borderline impossible.1 Only after Ethereum was introduced, smart contracts entered common parlance. But even recent blockchains offer execution environments much more constrained than those available on desktop computers, servers or even home appliances such as routers or NASes. Things are no different on Solana. I’ve previously discussed its transaction size limit, but there’s more: Despite using the ELF file format, Solana Virtual Machine (SVM) does not support mutable global state. Meanwhile, to connect Solana and Composable Foundation’s Picasso network, I was working on an on-chain light client based on the tendermint crate. The crate supports custom signature verification implementations via a Verifier trait, but it does not offer any way to pass state to such implementation. This became a problem since I needed to pass the address of the signatures account to the Ed25519 verification code.2 This article describes how I overcame this issue with a custom allocator and how the allocator can be used in other projects. The custom allocator implements other features which may be useful in Solana programs, so it may be useful even for projects that don’t need access to mutable global state. When dealing with colour spaces, one eventually encounters the XYZ colour space. It is a mathematical model that maps any visible colour into a triple of X, Y and Z coordinates. Defined in 1931, it's nearly a century old and serves as a foundation upon which other colour spaces are built. However, XYZ has one aspect that can easily confuse programmers. You implement a conversion function and, to check it, compare its results with an existing implementation. You search for an online converter, only to realise that the coordinates you obtain differ by two orders of magnitude. Do not despair! If the ratio is exactly 1:100, your implementation is probably correct. This is because the XYZ colour space can use an arbitrary scale. For example, the Y component corresponds to colour’s luminance but nothing specifies whether the maximum is 1, 100 or another value. I typically use 1, such that the D65 illuminant (i.e. sRGB’s white colour) has coordinates (0.95, 1, 1.089), but a different implementation could report them as (95, 100, 108.9). (Notice that all components are scaled by the same factor). This is similar to sRGB. In 24-bit True Colour representation, each component is an integer in the 0–255 range. However, a 15-bit High Colour uses the 0–31 range, Rec. 709 uses the 16–235 range and high-depth standards might use the 0–1023 range. A closely related colour space is xyY. Its Y coordinate is the same as in XYZ and can scale arbitrarily, but x and y have well-defined ranges. They define chromaticity, i.e. hue, and can be calculated using the following formulæ: x = X / (X + Y + Z) and y = Y / (X + Y + Z). Both fall within the [0, 1) range. Four years ago I proclaimed that regular expressions were broken. Two years ago I discussed this with BurntSushi and even though his expertise in the subject could not be denied, he did not manage to change my opinion. But now, two more years after that, I adjusted my stance. Everything factual I’ve written previously is still accurate, but calling regular expressions broken might have been a bit too much of a hyperbole. There’s definitely something funky going on with regex engines but I’ve realised an analogy which makes it make sense. Implementing Solana IBC bridge, I had to deal with various constraints of the Solana protocol. Connecting Solana to Composable Foundation’s Picasso network, I needed to develop an on-chain light client capable of validating Tendermint blocks. This meant being able to validate 50 signatures in a single transaction. Turns out that’s not possible on Solana and it’s not exactly because of the execution time limit. The real culprit is the transaction size limit which I’ve discussed previously. This article describes how signature verification is done on Solana, the limit on the number of signatures that can be verified in a single transaction and how that limit can be worked around. Solana transactions are limited to 1232 bytes which was too restrictive when I was implementing Solana IBC bridge while working at Composable Foundation. The smart contract had to be able to ingest signed Tendermint block headers which were a few kilobytes in size. To overcome this obstacle, I’ve used what I came to call chunking. By sending the instruction data in multiple transactions (similarly to the way Solana programs are deployed), the Solana IBC smart contract is capable of working on arbitrarily-large instructions. This article describes how this process works and how to incorporate it with other smart contracts (including those using the Anchor framework). In September 2022, ‘Théâtre D’opéra Spatial’, a work submitted by Jason Allen, won Colorado State Fair’s annual fine art competition in the digital art category. What made the success noteworthy was that the image had been AI-generated. Mr Allen eventually tried to register the work with the US Copyright Office but his attempts turned out fruitless. In September 2023 the Office refused his registration.  First, ‘Théâtre D’opéra Spatial’ by Jason M. Allen. First, ‘Théâtre D’opéra Spatial’ by Jason M. Allen.
Second, ‘A Recent Entrance to Paradise’ by Steven J. Thaler’s Creativity Machine. I didn’t think much of it at the time. I wasn’t that invested in the consideration of what kind of ‘two-dimensional artworks’ are protected by copyright and, more notably, I somewhat agreed with the decision. Perhaps the prompt was protected, but if only minor manual edits were made to the image, it felt like a stretch to say the image as a whole could be covered by copyright law. * available in Rust nightly. There are several aspects of Rust that I’m not particularly fond of but the one that takes the cake is core::io::BorrowedBuf which I despise with passion. It’s a nightly feature which puts in question my extreme emotions about it. On the other hand it means there’s time to stop it from getting stabilised and figure out something better. In this article I’ll describe the problem the feature addresses, the issues I have with the solution and describe some alternatives. As it turns out, things aren’t as easy as they seem on the first look. In 2023 UniSuper, an Australian retirement fund, decided to migrate part of its operations to Google Cloud. As port of the migration, they needed to create virtual machines provisioned with limits higher than what Google’s user interface allowed to set. To achieve their goals, UniSuper contacted Google support. Having access to internal tools, Google engineer was able to create requested instances. Fast forward to May 2024. UniSuper members lose access to their accounts. The fund blames Google. Some people are sceptical, but eventually UniSuper and Google Cloud publish a joint statement which points at ‘a misconfiguration during provisioning’ as cause of the outage. Later, a postmortem of the incident sheds even more light on events which have transpired. Turns out that back in 2023, Google engineer used a command line tool to manually create cloud instances according to UniSuper’s requirements. Among various options, said tool had a switch setting cloud instance’s term. The engineer omitted it leading to the instance being created with a fixed term which triggered automatic deletion a year later. So, human error. Scold the engineer and case closed. Or is it? |
|---|
|
|---|